Security In Seconds: The Hidden Node Problem and How It Can Be Used to Circumvent Your Wireless Security
There are two different types of attacks that will be described in this article that are tough to detect based on the hidden node problem.
Denial-Of-Service Attack
The first scenario, resulting in a denial-of-service attack, will consist of two devices and an access point, which we will call Device A, Wireless Access Point B, and Attacker Device C.
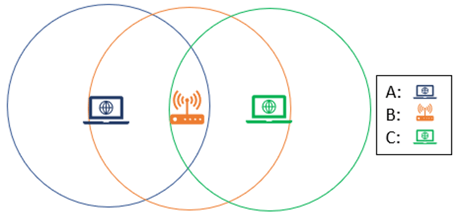
To describe what we are showing here, Device A can communicate with Wireless Access Point B, and Attacker Device C can communicate with Wireless Access Point B, but Device A cannot communicate with Attacker Device C. These nodes are considered hidden. Now why is this a problem?
The Hidden Node Problem
If Device A and Attacker Device C were both connected to the same Wireless Access Point B, they would be unable to communicate with each other, which means that the attacker can flood the communication medium and stop Device A from being able to communicate with Wireless Access Point B. If Device A is unable to communicate, then Attacker Device C has successfully carried out a denial-of-service against Device A, which ultimately should kick Device A off the wireless network.
Evil Twin Attack
In this next scenario, we are going to flip the roles, and instead of having two devices connecting to the same wireless network, we are going to have two wireless networks within range of the same device. Wireless Access Point A will be the real corporate wireless network, where Wireless Access Point C is an attacker’s access point trying to trick Device B into connecting to their network in an effort to breach Wireless Access Point A through an evil twin attack.
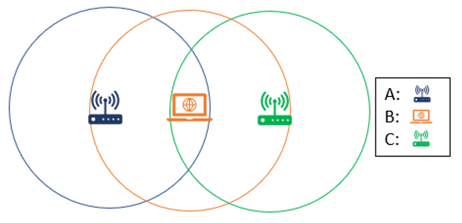
Through some simple traffic analysis attacker C would be able to easily identify the network name of Wireless Access Point A, and trick Device B into joining Wireless Access Point C, compromising Device B. The attacker could then wait for Device B to rejoin Wireless Access Point A, and compromise the corporate network. Because Wireless Access Point C is not in range of wireless network A, it would be impossible to identify this attack taking place, which would not only make the attack subtle, but allow the attack to persist.
There is a reason why most security breaches take months to detect, and that’s because attackers are accessing networks through legitimate means. The only way to spot this attack would be to monitor the communications between Device B, and hope to catch the traffic being sent to Wireless Access Point C and confirm that C’s device fingerprint, or signal strength, does not match that of Wireless Access Point A, which wireless intrusion prevention systems (WIPS) are not doing today.
How can the hidden node problem be mitigated?
Sonar identifies and notifies on potential anomalies & attacks (including rogue & fake access points, device spoofing & denial of service attacks).

Tim Connell
As Head of Enterprise Products for Pulsar Security, he guides the team in creating solutions which satisfy the needs of real-world customers, specializing in the areas of data management, storage network visibility, and enterprise security. Tim holds technical certifications as an Offensive Security Certified Professional (OSCP), CompTIA Network+, CompTIA Security+, GIAC Penetration Tester (GPEN), GIAC Web App Penetration Tester (GWAPT), and GIAC Python Coder (GPYC).




