Types of Cyber Threats to the Enterprise
Cyberspace has become a war frontier for nation-states, associated proxies, organized cybercrime groups, hacktivists, cyber terrorists, and other malicious actors seeking to gain the upper hand. Today, the increased connectivity of the Internet of Things (IoT) and network devices and the rapid spread of advanced digital technologies make it possible for state-sponsored malicious actors and other groups to engage in cybercrime activities, creating real-world impacts.
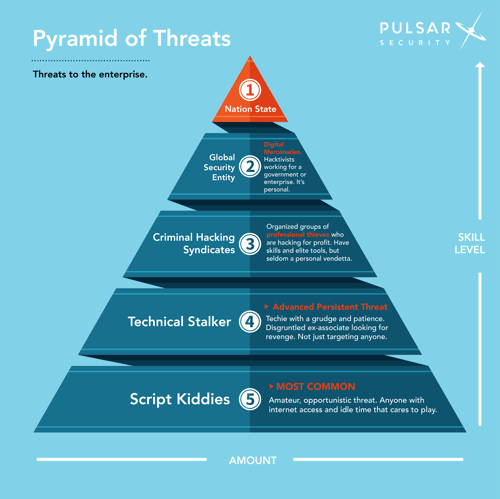
Pyramid of Threats Graphic
The following are the top threats facing enterprises today:
1. Nation State Threats
WHO ARE THEY?
Almost everyone has heard about state-sponsored cyber attacks from countries like Russia, China, North Korea, and Ukraine. Nation-state adversaries engage in aggressive cybercrime activities to target and compromise private and government networks to steal, destroy, and exfiltrate sensitive information. Additionally, nation-state threats cause harm to victim countries or corporations through activities like creating and disseminating fake personas or profiles, targeting supply chains for long-term spying and attacks, and spear-phishing techniques. Most nation-state threats leverage advanced technologies, subterfuge, and stealthy malware to wage cyberwar against other nations and multinationals.
WHAT IS THEIR GOAL?
Most state-sponsored cyber-attacks target critical infrastructures, military, businesses, and governments to render them nonfunctional. In most cases, it is a challenge to identify and apprehend perpetrators since they use advanced resources to cover their tracks to remain undetected. Also, nation-state threats often shift blame to rival cybercrime groups, hacktivists, or other foreign entities. The purpose and motivation of nation-state threats include but are not limited to military espionage, manipulating a country’s critical decision-making processes, and spreading disinformation through social media to influence public opinion.
WHO DO THEY TARGET?
According to a 2021 Microsoft report, at least 58% of state-sponsored cyberattacks can be traced to Russia, while North Korea, Iran, and China account for 23%, 11%, and 8% of nation-state threats, respectively. The Microsoft report also revealed that 80% of state-sponsored attacks target think tanks, intergovernmental organizations, non-governmental entities, and governments. The United States bore the brunt of nation-state threats as the report found that it has been a victim of 48% of the attacks. Also, a recent study from the University of Surrey shockingly revealed that nation-state threats increased by 100% between 2017 and 2020. The study also found that the enterprise is the largest and most common target of state-sponsored attacks (35%), while cyber defense comes in second with 25%. Additional findings from the study include:
- 64% of professionals in an expert panel agreed that 2020 saw a worrying increase of nation-state threats, with 75% indicating that most state-sponsored attacks attempted to exploit advantages resulting from the COVID-19 pandemic.
- Nation-state threats targeting supply chains increased by 78% in 2019, with more than twenty-seven distinct nation-state attacks involving supply chains between 2017 and 2020.
- More than 40% of nation-state attacks targeted critical assets with digital and physical components, such as energy plants.
- The study found damning evidence that nation-state threats are piling zero-day security flaws and that 10-15% of malware purchased on the dark web goes to adversaries acting on behalf of clients like nation-state actors.
2. Global Security Entity
WHO ARE THEY?
The use of mercenaries, often called digital mercenaries or cyber mercenaries, provides cyber space-related services, such as conducting espionage and exfiltrating corporate or government data. Nation-states and enterprises can engage digital mercenaries or hacktivists in diverse proxy relationships that involve defensive and offensive cybersecurity operations. For example, multinational corporations may hire cyber mercenaries to secure critical networks and infrastructure deployments. Also, nation-states may employ them to weaken military capabilities and capacities or undermine the integrity of another country. These cyber actors performing cyber-attacks on behalf of global entities can cause extensive damage remotely across different jurisdictions and are categorized to be undertaking mercenary-related activities.
WHO WILL THEY WORK FOR?
For example, Saudi Arabia’s ruler employed the services of cyber mercenaries to stifle dissent by using spying technologies obtained from an Israeli company. Currently, organizations with vast resources and the tiniest of countries can purchase cyber espionage services from global security entities, enabling them to execute complex operations, such as influencing political campaigns and electronic eavesdropping. Israeli-based firm NSO and Emirati company DarkMatter exemplify the propagation of global security entities in privatized spying. Such firms have enabled governments and corporations to target criminal elements, such as drug cartels and terrorist organizations. However, they have also acted on dark impulses in cybercrime activities that target journalists and activists.
Due to the rapid proliferation of a global high-tech cyberspace battleground, where armies of digital and cyber mercenaries target victims on behalf of well-paying clients, cybersecurity industry leaders have warned of a chaotic and dangerous future. Robert Johnston, a primary investigator of Russia’s involvement in the hack of the DNC and the founder of Adlumin cybersecurity firm, said that “even the smallest country, on a very low budget, can have an offensive capability.” “The barriers to entry in this space are getting lower and lower,” he added.
3. Criminal Hacking Syndicates
WHAT ARE THEY?
Criminals hacking syndicates consist of organized, professional cyber adversaries that hack for profit. They possess the requisite skills and elite tools but seldom a personal vendetta. The potential profitability of cybercrime has motivated well-organized networks of criminal hacking syndicates to collaborate in executing massive hacks to pull off major heists that would otherwise be impossible for individual hackers. Organized cybercrime continues to evolve and adapt as hacking syndicates devise more sophisticated methods of exploiting sensitive business data and personal information. Similar to the traditional organized crime groups, hacking syndicates follow leaders with the ideas, contacts, and influence to execute far-reaching hacks and attacks.
HOW DO THEY OPERATE?
Experts estimate that cybercrime will cost the world more than $6 trillion by 2021, largely attributed to organized cyber gangs and hacking syndicates. Furthermore, due to criminal hacking syndicates joining forces, there is a 0.05% likelihood of detecting, apprehending, and prosecuting them. This makes sense since it is challenging to estimate the penetration of criminal hacking syndicates since cybercriminals often do anything to cover their tracks and evade being caught. However, most cybersecurity experts agree that criminal hacking syndicates have grown in size and complexity and often operate as legitimate businesses. For example, organized hacking groups use organizational charts to plan and execute attacks targeting C-level executives and entire corporate departments.
WHO IS INVOLVED?
A recent paper by RAND Corporation’s National Security Research Division reveals key insights into why criminal hacking syndicates have increased in size and complexity. Specifically, the paper details that the hacker market consisted of a varied landscape of a network of individual hackers motivated by the need to prove themselves but has since metamorphized into a playground for highly sophisticated and financially driven hacker groups. Earlier hackers consisted of 17-year-old kids, while the average age of hackers today is thirty-five years. Besides, 80% of black-hat hackers are part of a criminal hacking syndicate. In the words of Marc Goodman, a global security strategist, individuals are choosing hacking as a profession. This radical shift has “led to the creation of increasingly sophisticated criminal organizations that operate with the professionalism, discipline, and structure of legitimate enterprises.”
4. Technical Stalker
WHO ARE THEY?
In most cases, hacks that make news headlines involve organized cybercriminals that steal data or money for financial gains. Other attacks employ hacking skills to make political or religious statements, such as hacktivists. However, there is another group known as technical stalkers whose primary motivation is an obsession. They include individuals with a grudge, such as disgruntled ex-associates, and have the patience to leverage advanced persistent threats to get their revenge.
HOW DO THEY OPERATE?
For example, a technical stalker doesn’t just target anyone. Technical stalkers may develop fixated interests in a specific individual due to particular reasons, including dismissal from work. Due to the obsession, a technical stalker may perform extensive reconnaissance by tracking an individual’s online activities to gather as much personal information as possible. Eventually, technical stalkers may require additional information on their victims, such as private pictures, telephone numbers, and home addresses. Failing to acquire the victim’s data from social media or online platforms may motivate them to become hackers.
5. Script Kiddies
WHO ARE THEY?
A script kiddie is a disparaging term used to describe a malicious hacker with insufficient hacking experience. As a result, they utilize existing software to launch and execute cyberattacks. Professional hackers usually develop sophisticated hacking tools, but script kiddies often leverage off-the-shelf tools and scripts to compromise a target. Most cybersecurity experts consider script kiddies to have lesser experience than white hat hackers and penetration testers since they lack sufficient understanding of computer networking and software. Essentially, script kiddies depend on scrips created by more experienced hackers since they lack the experience or knowledge to create their scripts.
HOW DO THEY OPERATE?
In addition, script kiddies search for and target the easiest routes through which they can compromise a system. Also, they don’t invest a lot of energy, finances, or ideas when perpetrating attacks. In this case, they may decide to use hacking projects developed by other programmers. For example, it is common to find script kiddies participating in hacking forums or gaming communities using common hacking tools, such as low-orbit ion cannon, to execute DDoS attacks on a game server. Such off-the-shelf programs are easy to find and acquire on the internet.
WHO ARE WE?

Patrick Hynds - Chief Executive Officer
Patrick serves as the team’s primary creative and strategic influence. As a recognized technology leader with expertise in Microsoft technologies, software development, network architecture, and enterprise security, Patrick is a frequent speaker at technical events throughout the world such as TechEd Hong Kong, Microsoft Security Conference, and Code Camp, and has spent two decades as a Microsoft Regional Director. A graduate of West Point and a Gulf War veteran, Patrick’s mission is to marry his leadership capabilities and deep technical experience in the pursuit of entrepreneurial ventures.




