Best Practices for Securing Your Home Network
Many cybersecurity risks threaten the security of your home network. An average household has at least 22 devices connecting to the home network at any given time, which provides attackers with multiple entry points. These include laptops, smartphones, smart fridges, and streaming devices.
Hackers target devices with weaker security and exploitable vulnerabilities to penetrate the home network and steal sensitive data stored in any device connected to the network.
Furthermore, as more people opt for hybrid and work-from-home strategies, attackers often target home networks to gain access to corporate network resources. In effect, it is essential to keep your home network secure.
Importance of securing the home network
Personal devices that connect to the home network store highly sensitive information, such as bank information, credit card data, login credentials, and personal data.
Data is a valuable commodity for the cybercrime world, and hackers utilize sophisticated methods to breach and exfiltrate it to their servers. Malicious actors can use such data for harmful intents, such as stealing your identity and launching targeted phishing attacks.
Fortunately, a secure home network reduces the likelihood of being breached and prevents cybercriminals from gaining access to your sensitive information.
Meanwhile, modern thermostats, TVs, computers, cameras, and other devices have one thing in common – they access the internet through your home network. The routers and modems provide a gateway between the devices and the internet. Failing to implement robust security measures to secure them is akin to leaving a door open for bad actors to gain unauthorized access and take control of your home network. Besides, the connected devices expand the attack surface. Protecting your home network reduces the attack surface, thus minimizing the risks of an attack.
Who is responsible for securing a home network?
According to recent research, more than one cyber threat affects 67% of home networks monthly.
Securing the home network is vital to maintaining the resiliency of connected devices to withstand attacks and prevent sensitive information from falling in the wrong hands.
Unfortunately, home networks are becoming increasingly hard to protect as homeowners deploy more connected devices, most of which cannot run security software.
The following chart shows how connected devices distribute cyber threats in the typical home network.
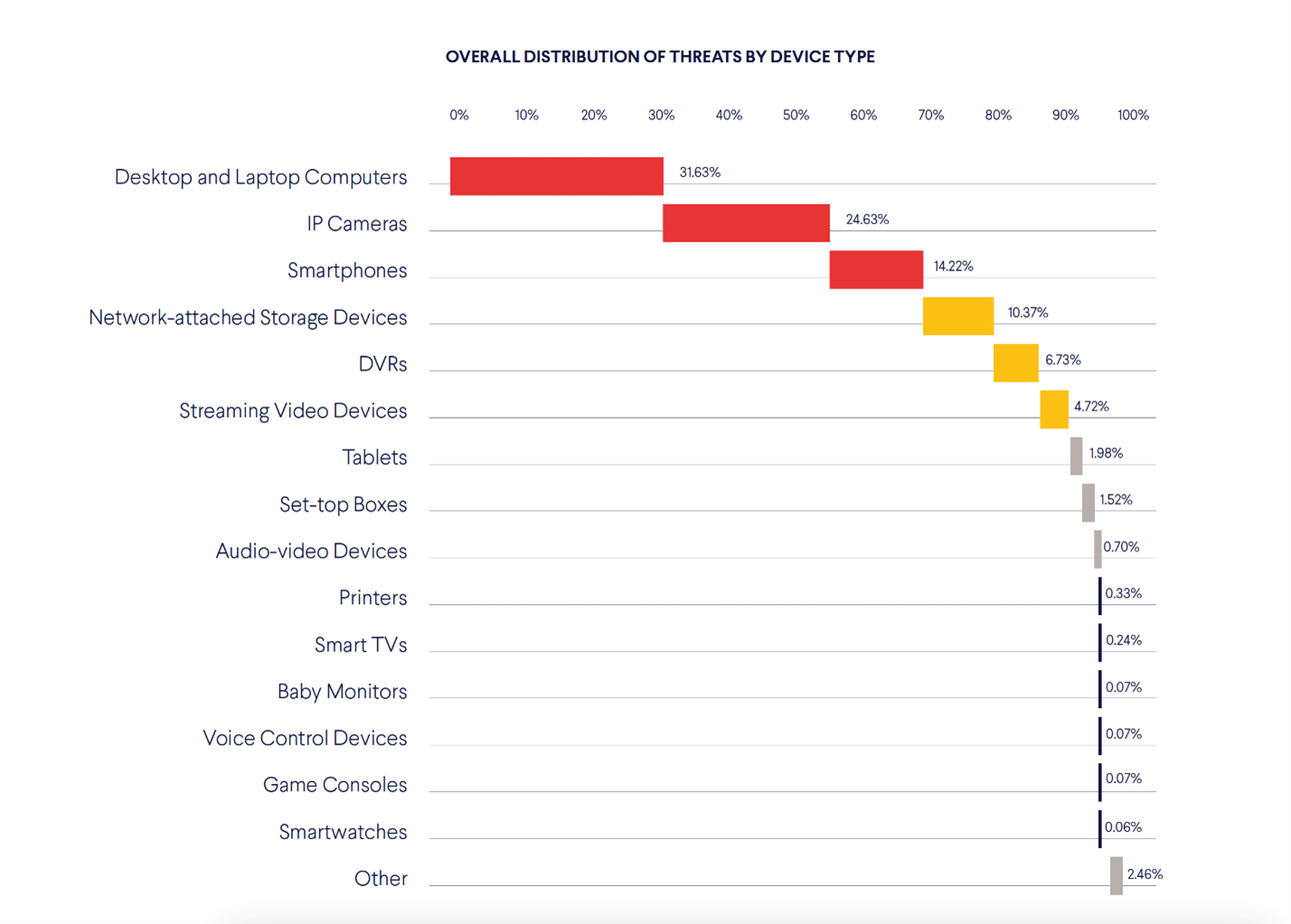
Each device represents different security flaws and attack surfaces, and this expanding diversity of connected devices has significantly altered the network security landscape.
Today, the threats targeting home networks range from DDoS attacks to automated hacks that detect and exploit vulnerabilities. Other threats include botnets, malware, and social engineering attacks.
Meanwhile, defending against evolving threats requires an extensive blend of cybersecurity measures, most of which are not accessible to homeowners or require advanced implementation skills. Evidently, most homeowners lack the technical skills and capabilities to secure each device connected to their home networks or deploy and maintain network-wide security measures.
In a 2021 survey, 48% of homeowners in the US admitted that they find it challenging to secure their home networks, and 21-36% said that they are unaware of how to strengthen their home network security.
Therefore, while consumers have a crucial role in bolstering the defenses of their home networks, they must also consider specialized services from security companies with the relevant experience, resources, and technical know-how needed to protect against a wide range of security threats.
Recommended practices for protecting the home network
The National Security Agency recommends the following measures to secure home networks from modern threats:
Device security measures
Use up-to-date operating systems.Keep your operating system up-to-date with the latest version and patches. The latest OS contains default security features that can prevent attacks. Ensure that IoT devices on your home network are updated regularly, and enable automatic updates if possible.
Protect routing devices.
Use a personal router device to gain administrative control over your home network and create a separate network for guests. It's important to keep your router device up-to-date with the latest patches and updates and replace it when it reaches its end-of-life (EOL) for support.
Enable WPA3 of WPA2.
Use Wi-Fi Protected Access 3 (WPA3) or WPA2 with a strong passphrase of at least twenty characters to secure the network communications. Enable protected management frames for added security.
Segregate the home network.
Segregate your wireless network into primary, guest, and IoT networks to prevent less secure devices from communicating with more secure ones.
Implement firewall measures.
Ensure your router has basic firewall capabilities and supports network address translation (NAT) to prevent internal system scans. If necessary, purchase a router that provides these capabilities. Ensure that your router supports IPv6 firewall capabilities if your ISP uses IPv6.
Implement security software.
Use security software with anti-virus, anti-phishing, anti-malware, safe browsing, and firewall capabilities. Also, use endpoint detection and response software to prevent the execution of malware attacks. Use full disk encryption on laptops, tablets, and mobile phones, and protect passwords by making them strong, unique, and not stored in plain text.
Restrict the use of the admin account.
Limit the use of the administrator account to prevent malware from accessing all files and configurations.
Protect against eavesdropping attacks.
Be cautious of home assistants and smart devices with microphones and cameras, and mute or cover them when not in use.
Observe secure user practices.
Backup data on external drives and store them securely. Avoid connecting devices to public charging stations and turn off or disconnect their Internet connections when not in use for an extended period. Finally, limit administration to the internal network only and disable the ability to perform remote administration on the routing device to prevent network compromise.
Best online behavior secure practices
Observe email best security practices.Email is a common target for cyberattacks. Avoid opening attachments or links from unsolicited emails. Check the sender's identity through secondary methods and delete the email if verification fails.
If an email contains embedded links, open a browser and navigate to the website directly or search for it using an Internet search engine. Use a different password for each account to prevent reusing any compromised passwords. Always use secure email protocols, particularly if using a wireless network. Configure your email client to use the transport layer security (TLS) option to encrypt your email in transit between the mail server and your device.
Use a modern, up-to-date browser.
Use modern and updated browsers that provide prompts for security features. When conducting sensitive activities like financial transactions or logging into accounts, ensure that the browser's URL tab displays a lock icon to indicate secure transit.
Observe security precautions on social networking sites.
Take precautions when using social networking sites, such as limiting access to personal information, being cautious of duplicate profiles, and reviewing security policies and settings.
Use strong authentication.
Implement strong authentication safeguards. These include enabling strong authentication on the router, using password managers, and using multi-factor authentication whenever possible.
Avoid exchanging work and home content.
Avoid exchanging information between home and work systems through email or removable media to prevent attackers from compromising work systems. Instead, use organization-provided equipment and accounts while working remotely or follow corporate-mandated security products and guidance for accessing corporate resources on personal devices.
Also, instead of transporting files between devices, connect to a remote desktop or terminal server inside the corporate network. Use a VPN or other secure channel to connect to corporate networks and services, and avoid using personal accounts for business interactions.
You can also consider using separate devices for different activities, such as financial/PII and entertainment.
About Pulsar Security
Pulsar Security is a team of highly trained and qualified ethical hackers whose job is to leverage cybersecurity experience and proprietary tools to help businesses defend against malicious attacks. Pulsar is a Veteran, privately owned business built on vision and trust, whose leadership has extensive military experience enabling it to think strategically and plan beyond the problems at hand. The team leverages offensive experience to offer solutions designed to help analyze and secure businesses of all sizes. Our industry experience and certifications reveal that our engineers have the industry's most esteemed and advanced on the ground experience and cybersecurity credentials.

Jill Stagner
Jill is the Director of Marketing and Program Development. She manages the marketing, communication and company branding efforts for Pulsar. In addition, she helps with the public facing materials for all of Pulsar’s products and services.




