Ransomware | Common Types & Prevention Techniques
We hear about ransomware attacks all the time. But what exactly are they, and should you be concerned for your business? Are there ways to prevent these attacks from happening?
What is Ransomware?
Ransomware is a type of malicious software that attackers use to encrypt files and block access to systems. These attackers will then demand ransom money from victims in exchange for releasing their data and systems. Needless to say, the motive for ransomware attacks is usually monetary, and unlike in other types of attacks, ransomware authors usually notify the victims that an exploit has occurred, along with instructions for how their victims can recover from the attack. Bad actors often demand ransom in virtual currencies, especially Bitcoin, to keep their identities hidden.
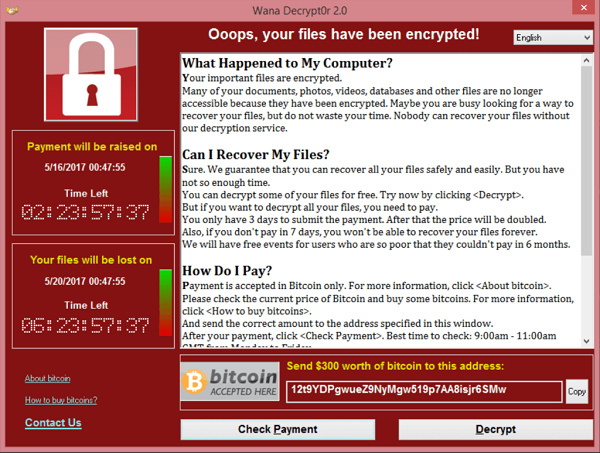 WannaCry Ransomware Attack, Wikipedia
WannaCry Ransomware Attack, Wikipedia
Why do hackers demand virtual currencies?
Bitcoin is the most widely used digital currency today, and most cybercriminals nowadays demand ransom in it rather than some physical currency. Apart from being untraceable, Bitcoin is also not overseen by any government bodies or banks. What's more, sending, receiving, and converting cryptocurrency to cash does not require hackers to reveal their personal information.
How does an attacker spread ransomware?
Customarily, hackers spread ransomware through malicious attachments found in emails or infected malicious software apps. Additionally, they use infected external storage devices and compromised or spoofed websites to launch malware. Other than phishing emails and infected software apps, attackers have used Remote Desktop Protocol (RDP) and other techniques that do not rely on any form of human interaction to spread ransomware.
Hackers also use other aggressive ways to launch and spread ransomware - for instance, they can create vulnerabilities to exploit security holes in a system, or develop ransomware that can spread through chat messages and browser plugins.
With sophisticated ransomware distribution tactics, it comes as no surprise that ransomware perpetrators are carrying out more than 4,000 attacks daily, while organizations are paying an average ransom of $233,217. Besides the financial loss, there is an average 19 day downtime following a ransomware attack.
Types of Ransomware Attacks
1. Locker Ransomware
This form of ransomware blocks computer functions, such as desktop, keyboard, and mouse. Attackers in locker ransomware only allow victims to interact with the window displaying random demand messages, while other functions of the computer remain inoperable. Locker ransomware does not target critical files. Instead, this malware just wants to lock users out without compromising the victims' data. Ivy Wigmore writes on TechTarget that in Windows systems, locker ransomware also blocks access to system components, such as Windows Task Manager and Registry Editor, and the screen is locked until the victim pays the ransom.
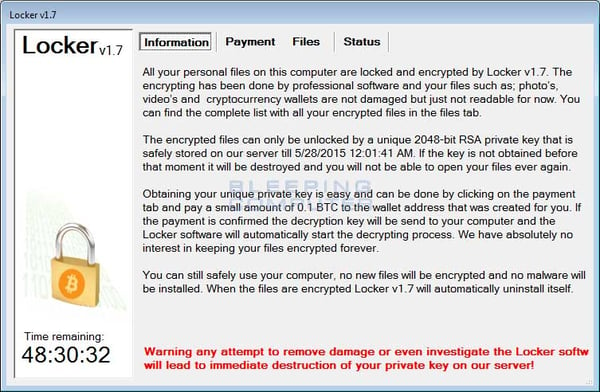 Locker Ransomware Attack, Bleeping Computer
Locker Ransomware Attack, Bleeping Computer
2. Crypto-Ransomware
Unlike the locker malware, crypto-ransomware aims to compromise the victim’s data by encrypting documents, videos, and pictures on the compromised system, but does not interfere with other computer functions. This attack tactic implies that users can still see their files but cannot open or edit them.
Crypto-Ransomware comes with an encryption key that expires after a set amount of time. If the countdown expires and the ransom has not been paid, the victim risks losing all of their encrypted data. As a result, many victims end up paying the ransom simply to get their data back.
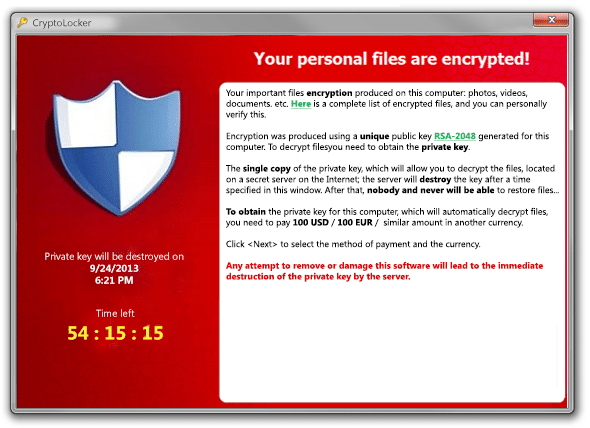 Crypto-Ransomware Attack, Bridewell Consulting
Crypto-Ransomware Attack, Bridewell Consulting
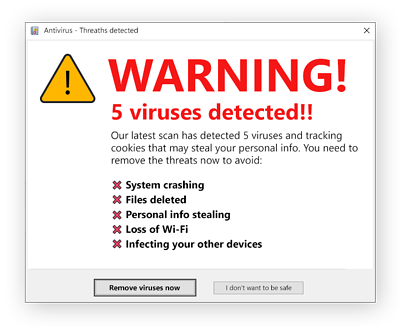
3. Scareware
Scarewaremalware poses as security software or tech support. Generally, victims receive pop-up notifications reporting malware has been discovered on their systems and devices. Certainly, security software that users do not own or have not installed in their devices would not have access to infections and other system information. By “scaring” the user to click on this pop-up, the user will install the ransomware.
Scareware Attack, AVG
4. Doxware/Extortionware
In a doxware attack, hackers threaten to publish victim data online if the victim fails to pay a ransom in the specified time. Ivy Wigmore writes on TechTarget, "Doxware, also known as extortionware, is a software used by a hacker to access the victim’s sensitive data and threatens to publish it if the victim does not meet their demands, which are typically for money.” The term doxware comes from doxing, which means accessing and publishing private information about an organization or individual.
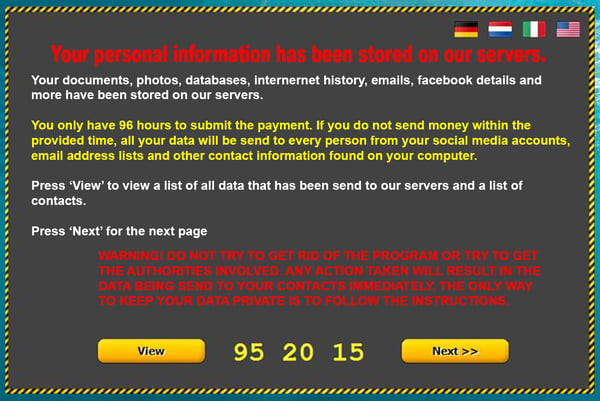
Doxware Popup, Raedts
5. Master Boot Record Ransomware
Master Boot Record (MBR) is a small program that executes every time the computer boots, even before the operating system loads. In an MBR infection, the ransomware encrypts the entire hard drive, not just the user's files, making it impossible to access the operating systems. Preksha Saxena writes that master boot record infection "extends the scope for deep infection and controls the infected computers, which make the attack more severe."
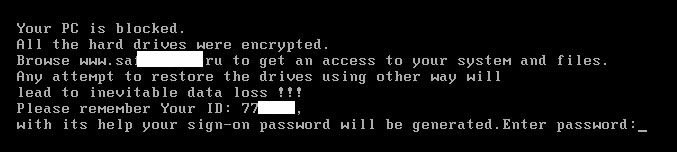
Master Boot Record Ransomware, SecureList
6. Mobile Ransomware
As the name implies, mobile ransomware affects mobile devices. In this case, an attacker uses the attack to steal data or lock a phone and require a ransom to return the data or unlock the device.
Well Known Ransomware Examples
So far, we have defined what a ransomware attack is and listed the main types of these forms of malware. Next, we will review some of the well-known examples of ransomware to help businesses explore and understand the risks posed by the attacks.
1. Locky
A group of organized hackers first used the Locky ransomware in an attack in 2016. The attack encrypted more than 160 file types and was spread through fake emails with infected attachments, a method commonly known as phishing. Locky ransomware target file types are often used by designers, engineers, developers, and testers. As a result, many users fall for the email trick and install the malware on their computers.
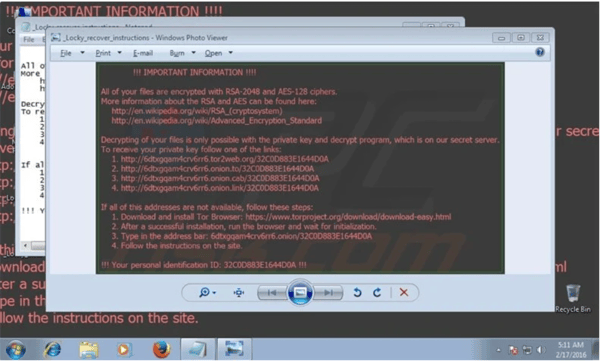 Locky Ransomware, PCRisk
Locky Ransomware, PCRisk
2. WannaCry
We cannot fail to mention the notorious WannaCry when talking about ransomware examples. The WannaCry malware attack spread to over 150 countries in 2017. Threat actors designed WannaCry to exploit Windows' security vulnerabilities, consequently affecting 230,000 computers worldwide. In particular, the WannaCry attack hit one-third of all NHS hospitals in the U.K., causing estimated damages of millions of dollars. Additionally, the incident locked out users and demanded a ransom payable in Bitcoin.
Most prominently, the WannaCry attack exposed the risk of operating outdated systems since cybercriminals exploited an operating system vulnerability for which a patch was available at the time of the attack. Overall, security experts estimate WannaCry's worldwide financial damage to be $4 billion.

WannaCry Ransomware Attack, Wikipedia
3. CryptoLocker
erhaps the main example of a widely spread attack that used public-key encryption is CryptoLocker – an attack that caught many enterprises off guard. According to a post by Nick Lewis, CryptoLocker is different from other ransomware because it uses modern attack techniques, such as delivering malware via an exploit kit on compromised websites. This malware also uses secure encryption that is difficult to reverse engineer.
CryptoLocker also encrypts data on the local machine and removable media and network shares. On top of that, attackers using the malware leverage servers on the Tor network to distribute keys, making their malicious activities untraceable. Surprisingly, CryptoLocker actors have evolved the payment process, letting their targets pay through various channels like Bitcoin and MoneyPak.
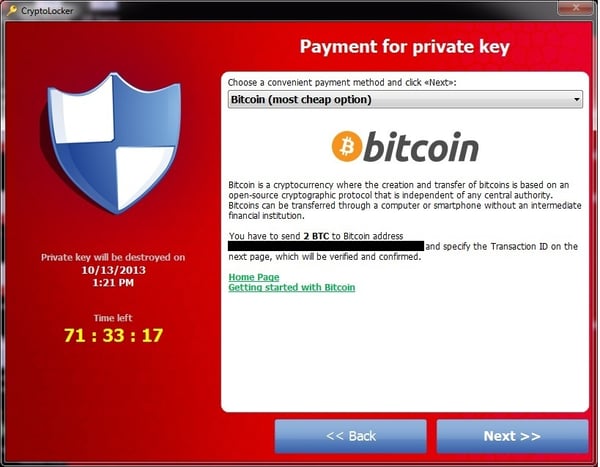 CryptoLocker Ransomware Attack, Wikipedia
CryptoLocker Ransomware Attack, Wikipedia
4. Petya Ransomware
Petya ransomware started spreading internally on June 27, 2017, targeting Windows servers, P.C.s, and laptops. Security analysts report that the attack appeared to be an updated variant of the Petya malware virus. The ransomware used the Server Message Block vulnerability that WannaCry employed to spread to unpatched devices, as well as the credential-stealing technique to spread to non-vulnerable machines.
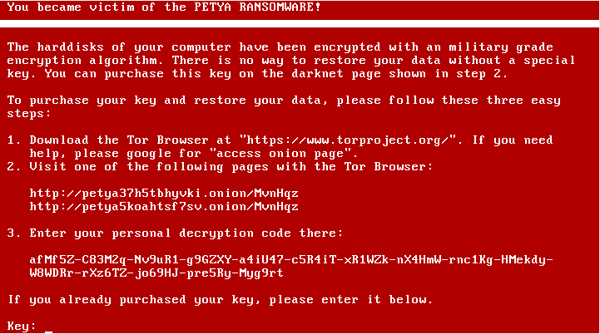
Petya Ransomware Attack, Wikipedia
Impacts of Ransomware Attacks
Who Do Ransomware Attacks Target?
It is essential to note that ransomware targets can vary from a single individual, to a small to medium-sized business (SMB) or enterprise-level organization, to an entire city or state. Recent incidents also suggest that public institutions are especially vulnerable to ransomware attacks. This observation has something to do with the fact that many public organizations lack the necessary cybersecurity measures to defend against attacks adequately. In addition to flawed cybersecurity strategies, public institutions handle irreplaceable information that could cripple them if encrypted. The same holds for small and medium businesses that operate with inadequate security controls.
What Are The Costs of a Ransomware Attack?
A recent post by Barbara Kay on Forbes reads, "ransom demands are up, and the cost of clean-up has doubled in the last year." Sophos' research also reveals the average cost of a ransom situation is ten times the ransom paid, in part due to down time, lost business, and allocation of resources. The impacts of such malware attacks can surely be devastating to a business. A Safe At Last blog post states that ransomware attacks can quickly turn into a nightmare for unprepared I.T. admins. "Cybercriminals are gaining so much control that they can sway even large organizations to dance to their tune and give in to their financial demands," writes Safe At Last.
Sophos discovered that the average cost of remediating a ransomware attack is a staggering $761,106. Based on this finding, paying cybercriminals the ransom money is apparently half the cost involved. By and large, companies need to pay for all the working hours required to restore systems, clean up the ransomware attack damage, and enhance their cybersecurity postures after recovery. Sophos also revealed that businesses that pay the ransom lose twice the amount due to all the additional costs, totaling close to $1.45 million.
Impact of the Ransomware Attack on the U.S. Colonial Oil Pipeline
On May 7, 2021, the U.S. Colonial Oil Pipeline shut down after a ransomware attack infected the systems at the company. Security reports show that the attack was launched by a threat actor known as DarkSide. As a result of the attack, the victim announced it was shutting off operations temporarily to prevent the ransomware spread. However, the shutdown of the 5,500-mile pipeline, the largest in the U.S., led to gas shortages in parts of the country. Apart from the shortages, The Wall Street Journal later revealed that Colonial Pipeline CEO authorized a $4.4 million ransom payment.
Apart from financial loss, other ransomware attacks effects include loss of business data, downtime because of compromised I.T. infrastructure, loss of productivity resulting from downtime, loss of potential revenue, and long-term damage to both information and systems. Moreover, the attacks can damage a company's previous reputation as secure. Finally, if the victim deals in public services like healthcare, there is a potential for personal harm.
Emerging Trends in Ransomware Attacks
Undeniably, the last two years have seen a surge of ransomware attacks against targets ranging from international meat producers, oil pipelines, and global technology enterprises to small and medium businesses. Attacks nowadays are more targeted, elaborate, advanced, and broader than before, with extremely detrimental impacts.
Ransomware As A Service (RaaS)
Hackers can currently purchase ransomware kits that allow them to create malware with specific capabilities. Additionally, the tools available on the deep web allow even attackers with little or no technical background to order inexpensive ransomware as a service (RaaS) and launch massive attacks with minimal effort.
Doxware
Hackers also innovate to come up with ways to coerce victims to meet the ransom demands. With ransomware becoming less effective and profitable as more organizations implement security measures such as backing up their data to prevent the loss, attackers are now turning to new ransomware types, such as doxware or extortionware. These types of attacks take a step further than just encrypting files. In particular, threat actors exfiltrate the data and explore it to find potential doxing targets. As Ivy Wigmore writes on TechTarget, "the hacker typically encrypts the victim's data and demands payments to relinquish the key, in addition to refraining from broadcasting the sensitive data."
Preventing and Responding to Ransomware Attacks
While early instances of ransomware attacks only locked access to components like Windows desktops and web browsers, and did so in ways that security experts could fairly easily reverse engineer and open, the present attacks feature strong, public-key encryption that denies access to files and systems.
- To protect against ransomware threats, organizations should back up computing devices regularly. Additionally, it is essential to inventory all assets to ensure that you back up all sensitive information.
- Installing and maintaining an updated security software can also prevent ransomware attacks. Modern anti-malware software effectively quarantines malware and ensures that attackers did not create a backdoor that can allow them to access the network or system at a later date.
- Train employees to spot and avoid clicking malicious links on emails and opening attachments from untrusted sources. Users should not download apps using third-party app stores. Additionally, they should keep mobile devices and apps up to date.
- Security experts recommend that organizations should avoid paying ransoms.
- Monitor network for suspicious activities.
Undoubtedly, there is no guarantee that you can stop a ransomware attack and regain data. Fortunately, victims can stop and reboot their systems in safe mode to restore the system to a previous, non-infected state. Windows users can use the System Restore function that rolls Windows devices and their system files back to a certain marked point in time before the system was infected.
Should You Pay The Ransom Demanded in a Ransomware Attack?
Most law enforcement agencies staunchly recommend against paying ransomware to attackers, since in doing so, you are only inviting them to commit more ransomware attacks. The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) issued an advisory to warn organizations making or facilitating ransomware payments that they could run afoul of U.S. regulations and face stern penalties. According to the advisory, ransomware demands have increased during the COVID-19 pandemic as cyber actors target online systems that U.S. persons rely on to continue conducting business.
OFAC warns that companies facilitating ransomware payments to cyber actors on behalf of victims, including financial institutions, cyber insurance firms, and companies involved in digital forensics and incident response, encourage future ransomware payments demands and risk violating OFAC regulations.
Christopher Wray, the FBI Director, also encourages companies that are victims of ransomware attacks to avoid paying hackers to unlock their data. Instead, ransomware victims should quickly contact law enforcement, which opens the possibility of creative solutions. "It is our policy, it is our guidance from the FBI, that companies should not pay the ransom," Wray told the House Judiciary Committee at a hearing.
Enhance Your Cybersecurity with Pulsar Security
Pulsar Security team strongly believes it is more important than ever to protect against adversaries at the door before they get a chance to take hold and unfold their multi-faceted attacks. In effect, we provide technical solutions and expertise needed to face and eliminate the challenge.
Apart from our technical solutions, a look into the Pulsar Security team's industry experience and certifications reveals that our engineers have the industry's most esteemed and advanced on the ground experience and cybersecurity credentials. Besides that, having the credentials denotes proficiency in a global standard for effective and reliable cybersecurity.
Pulsar Security works with all types of companies to determine what is actually on their network, secure it, and game plan how attackers will try to break existing defenses. Overall, we do more than just run automated scans – we help our customers implement effective and sustainable processes for mitigating and managing risks.
Whether you are just building your security program to defend against threats like ransomware, need to assess the performance of your current efforts, or want us to simulate a live attack, we are here to help at every step.

Corey Belanger
Corey is a Security Consultant and leads QA of product development, using his expertise in these dual roles to more effectively test and secure applications, whether while building enterprise applications or while performing penetration tests and vulnerability assessments for customers. An Army veteran with a tour of duty in Afghanistan, Corey has built a post-military career in security while earning Network+, Security+, GIAC Certified Incident Handler, GIAC Python Coder, GIAC Web App Penetration Testing, and GIAC Penetration Tester certifications. Corey is also a BsidesNH organizer and founding member of TechRamp, avenues which he uses to help others build their skills for careers in security and technology. Fun Fact: When not manning a terminal or watching the Bruins, Corey can often be found snowboarding or riding his motorcycle.




