What Is An Evil Twin and How Do You Spot One?
Wi-Fi has been around for many years, yet little has been done to improve protection from wireless threats. One of the more common wireless threats is an Evil Twin Attack which can be very dangerous, and generally easy for an attacker to create.
What is an evil twin?
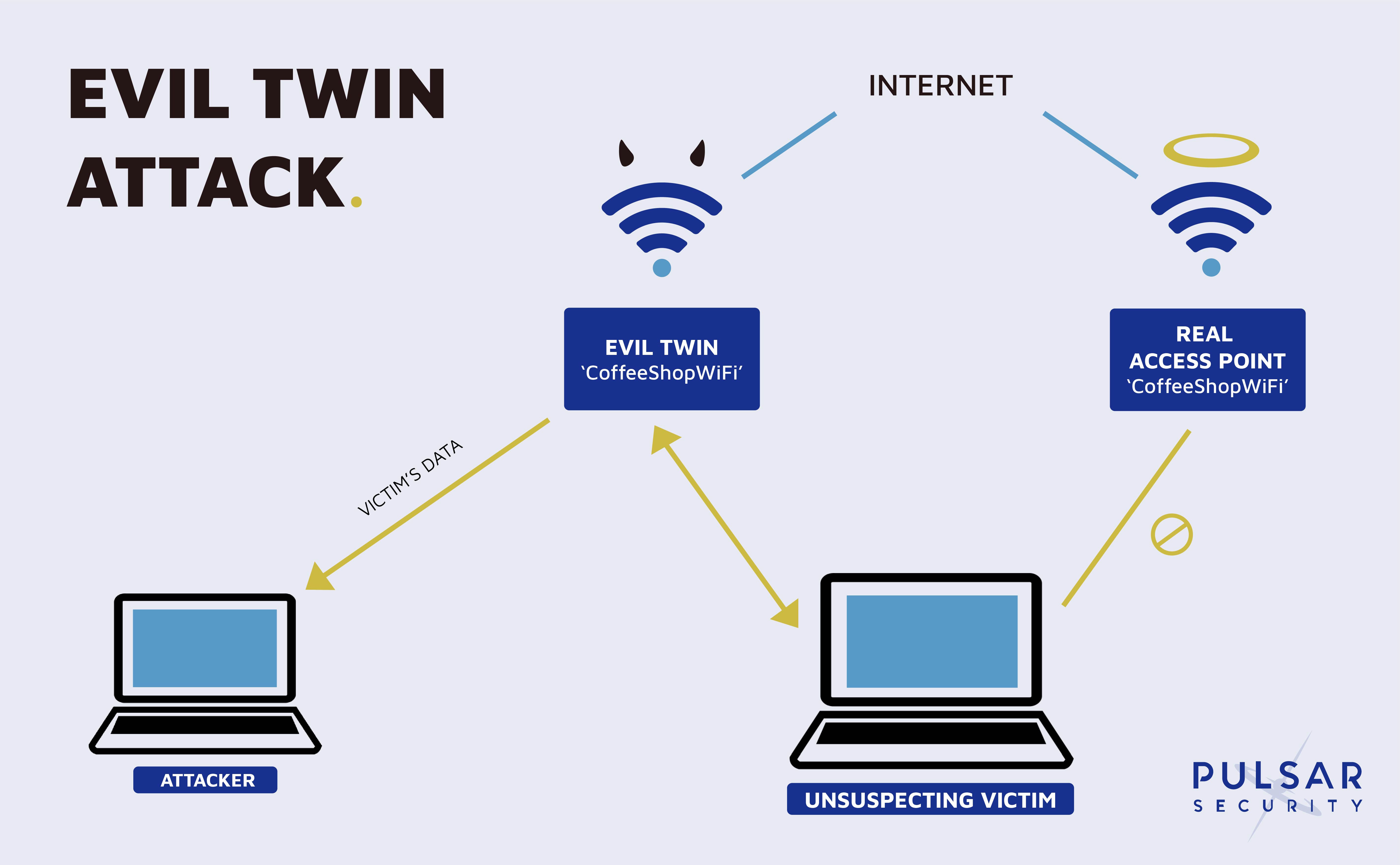
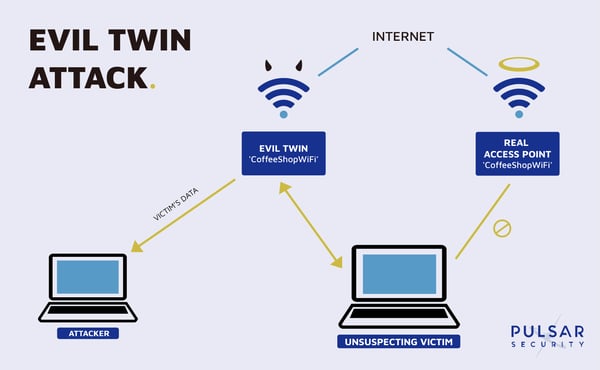
In a normal wireless connection, an access point broadcasts a network name, or SSID (Service Set Identifier). All access points (APs) that you have asked your device to "Connect Automatically" to will be on your PNL (Preferred Network List). Since your device is set up to remember PNLs, once the client device discovers the broadcast it will automatically connect to it.
An evil twin exists when an attacker broadcasts the same SSID as a legitimate access point. Devices are then fooled into connecting to the evil twin which creates a MitM (Man in the Middle) opportunity for the attacker. This attack makes open networks very dangerous. Any time a person connects to a hotel or coffee shop's Wi-Fi, they could really be connecting to an Evil Twin masquerading as that same Wi-Fi.
This attack becomes significantly more difficult if the wireless network is password protected, but it's still possible. For a private network that is PSK (Pre-Shared Key) encrypted, the attacker would need the hash from the WPA/WPA2 handshake. Although it isn't difficult to capture the hash, it still needs to be cracked, which is why it is important to have a strong password on your Wi-Fi network.
In the event that clients have the network saved and automatically connect to the access point, the attacker can initiate a Deauthentication Attack which sends de-authentication packets to the device and breaks the connection. The device will then automatically attempt to reconnect, but unknowingly connect to the evil twin.
What can you do to prevent this attack?
There are a couple of important things you can do to mitigate this attack from happening. In a corporate network environment, it becomes a lot harder as Evil Twin attacks can be difficult to detect and defend against.
1. Be careful what networks you are automatically connecting to.
2. Go through your device and delete the networks you have listed in your PNL, or preferred network list.
3. Do your best to avoid connecting to public networks. If you're in a situation where you are connecting to a public network, make sure not to transmit any sensitive information like logging into your bank account.
4. Use a VPN (Virtual Private Network) during Wi-Fi sessions outside of your home. If a VPN is not accessible to you, you can also use your Wi-Fi hotspot on your smart phone.
5. If you see a SSID being broadcasted that doesn't have a MAC address that's listed in your corporate inventory, this is an indicator of an Evil Twin Attack. Sometimes however, the attacker can even spoof the BSSID or MAC address to even better disguise itself.
6. Conduct an assessment or set up a service that monitors and protects your wireless networks, access points, and end points.
Pulsar Security's automated, 24/7/365 Wi-Fi network assessment service, powered by SONAR, can assist you with the wireless landscape surrounding your business so you can protect your Wi-Fi networks from potential attackers.

Corey Belanger
Corey is a Security Consultant and leads QA of product development, using his expertise in these dual roles to more effectively test and secure applications, whether while building enterprise applications or while performing penetration tests and vulnerability assessments for customers. An Army veteran with a tour of duty in Afghanistan, Corey has built a post-military career in security while earning Network+, Security+, GIAC Certified Incident Handler, GIAC Python Coder, GIAC Web App Penetration Testing, and GIAC Penetration Tester certifications. Corey is also a BsidesNH organizer and founding member of TechRamp, avenues which he uses to help others build their skills for careers in security and technology. Fun Fact: When not manning a terminal or watching the Bruins, Corey can often be found snowboarding or riding his motorcycle.