What is Red Teaming? Types of Information Discovered Through Red Team Assessments
Red teaming is the practice of adopting an adversarial approach to rigorously assess security plans, policies, systems, and assumptions. The red teaming originated in the military to realistically evaluate the strength and effectiveness of security strategies using an external perspective. So, what is a red team from a cybersecurity viewpoint? What are the benefits of red teaming, and how does it work? What types of information can you discover through red teaming?
What is the Purpose of Red Teaming?
"The goal of red teaming is to overcome cognitive errors such as groupthink and confirmation bias, which can impair the decision-making of critical thinking ability of an individual or organization," reads a post on TechTarget. Conspicuously, a red team aims to breach or compromise a company's digital security from a cybersecurity perspective.
A red team assessment is a goal-based adversarial initiative that requires a holistic view of an enterprise from an adversary's perspective. In effect, red teaming efficaciously demonstrates how real-world attackers can combine disparate exploits to compromise systems. Additionally, the process features important mechanisms for detecting vulnerabilities and hence enhancing the security of target systems by allowing system defenders to understand system weaknesses from an attacker's perspective.
Red team assessments are similar to penetration tests but take the "by all means necessary" approach to gain access to target networks and sensitive information. Red team activities simulate a realistic cyberattack using methods and techniques that real-world attackers use against businesses. That is why it is common to hear a red team member talk about "think like an attacker."
Red Teaming Benefits
- Evaluate your response competence to attacks – red teaming reveals how prepared your company is to respond to a targeted attack designed to test the effectiveness of technology, people, and process
- Discover and classify security issues – red teaming activities help organizations discover if their systems, data, and other critical assets are at risk. Moreover, the initiative reveals how easily attackers could target the crown jewels
- Unearth hidden threats and vulnerabilities – red team mirrors the latest adversarial tactics to identify hidden vulnerabilities that attackers seek to exploit
- Respond to discovered exposures – red teams provide essential post-operation support to address identified security issues to mitigate potential real-life data breaches effectively
- Enhance internal security team effectiveness – by simulating a range of attack scenarios, a red team can help your internal IT and security team to identify and address gaps in your security strategies
- Prioritize security investments – red teaming initiatives provide a better understanding of your organization's security weaknesses, guiding your investment approach to ensure that resources deliver the greatest benefit.
How Red Teaming Works
Typically, red teaming ties together seemingly small vulnerabilities in an attack path to show how such flaws can cause significant damage.
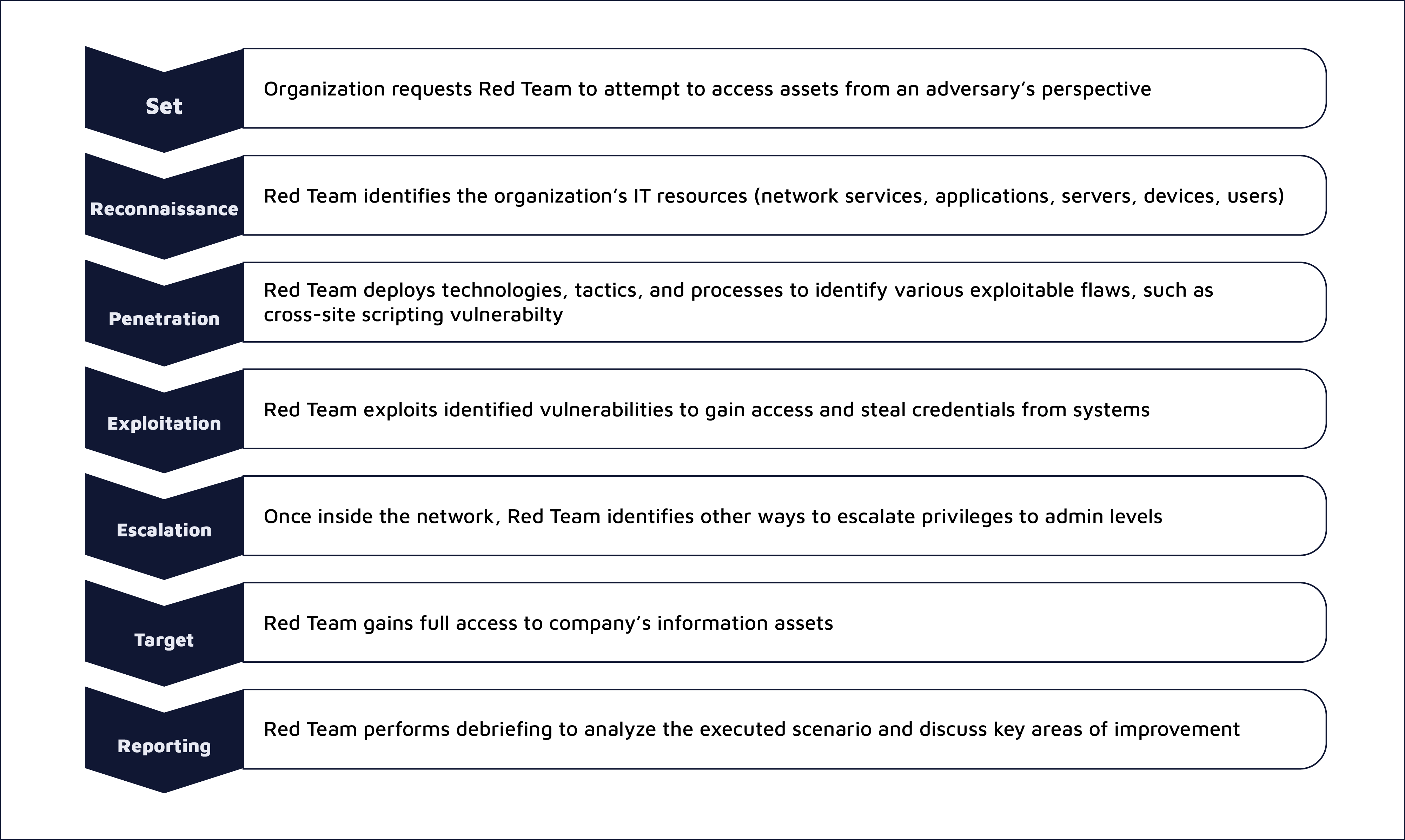
The first step in a red team activity is to identify and set goals. This stage involves coming up with flags to be met and the compilation of engagement rules that define the kind of cyberattacks allowed for the project. It is also crucial for a red team to determine any exceptions that will not be targeted on the attack surface. Eventually, it is vital to confirm the actual timeline for executing the red team exercises in conjunction with the client's needs on top of defining goals and engagement rules. Finally, some clients may issue a Letter of Authorization in the first step to grant explicit permission to conduct controlled cyberattacks on their assets and lines of defense.
Next, the team conducts an assessment to get a broad overview of the organization's IT and network infrastructures by taking the mindset of a real hacker. Naturally, the reconnaissance step, also known as intelligence gathering, reveals information about a company's digital and physical assets, stakeholders (C-suite, suppliers, partners, personnel, customers), technical processes, and operational processes. The step also uncovers information like the network IP address range assigned to an organization and the open ports and related services.
After discovering the assets, the red team conducts assessments to discover security vulnerabilities and the various cyberattacks they feel are necessary to exploit target networks and systems. In essence, the identified vulnerabilities and cyberattacks are not cast in stone. In that case, a red team can subsequently add in more threat vectors they deem appropriate even after the vulnerability assessment and penetration testing phases have actually started. Additionally, this step determines any subdomains hidden from public access, misconfigurations in cloud-based infrastructure, weak authentication forms, and lack of security awareness among employees.
After intelligence gathering, the red team launches attacks towards the intended targets. For instance, the team hits and exploits systems with known vulnerabilities, impacts sandboxing environments used in software development, and accesses any hardware residing in the network infrastructure, including workstations, wireless devices, servers, and network security tools.
Lastly, the red team documents and creates a final report, primarily consisting of discovered vulnerabilities, the types of cyberattacks launched, and the degree of exploitation. Besides, the team can provide corrective actions that the target can take to remediate all known and unknown security gaps and the consequences of not taking action by implementing recommended measures.
Based on the red teaming process, what information can you discover through a red team exercise? Firstly, the team identifies any physical, hardware, software, and human vulnerabilities affecting an organization's security. Apart from identifying the vulnerabilities, a red team focuses on exploiting some of them across multiple environments, including attempting to gain physical access to specific premises that a target business owns.
Secondly, a red team initiative obtains a realistic understanding of all the risks that an organization faces. In this case, a red teaming process with a wide scope reveals more vulnerabilities. Markedly, the exercise covers multiple security aspects, including procedures for guiding users, training used to enhance employee awareness, and the infrastructure used to secure a facility physically.
Red Team Composition
Typically, a red team may be a contractual external party or an internal group of IT employees and security experts to simulate malicious and adversarial actions. Additionally, the team composition is based on the premise that professionals can model adversaries to find systemic vulnerabilities in information systems that would otherwise go undetected.
The red team also features two very distinctive subgroups: the operational (working) team and the support team. The operational team usually is forward-deployed to conduct assessments and exploits actively. In effect, the team learns the target, researches the potential adversaries, and identifies vulnerabilities. Lastly, the working group defines an action plan based on the red team exercise. Characteristically, the operational group members include physical security experts, surveillance and recon experts, digital security specialists, OSINT experts, security generalists, and a team leader.
On the other hand, the support team stays back to prove intelligence to the operational team and coordinate the process with the customer. Simply put, the support group provides an extra set of eyes when needed. In this case, they perform the initial recon once the red team gains a foothold on the network. The support team comprises digital security experts, exploitation and code writing experts, systems and network experts, and a physical security countermeasure expert.
Pulsar Security Red Team Engagement
Of all the available cybersecurity tests and assessments, a simulated cyber attack by Pulsar Security is as close as you can get to understanding how prepared your company is to defend against a real-world persistent hacker.
Pulsar Security's Red Teaming aims to improve your asset's and personnel's readiness through a realistic security incident drill targeting your enterprise's cyber, human, and physical information security elements. During red teaming engagements, Pulsar Security's red team, composed of the best and brightest engineers in the industry, develops realistic attack scenarios using threat intelligence and other details relevant to your organization's IT infrastructure, premises, and personnel.
Logically, our red teaming attack scenarios are tied to specific, measurable, and tangible objectives tailored to your business. Additionally, we follow a defined structure that mimics the tactics, techniques, and procedures (TTP) of real-life adversaries. Consequently, we put your organization's IT personnel and incident response team, also referred to as the blue team, to the test.
After our red team operations, we perform a debriefing with your team to analyze the executed scenario and discuss key areas of improvement. Part of the process involves a sift probe of the lessons learned. Ultimately, we ensure you improve your security posture without breaking your defenses. Our red team engagement offers a cost-effective method to evolve and improve your defenses. Needless to say, the cost for the service is considerably less expensive than suffering a costly, damaging breach.
Why Choose Pulsar Security's Red Team?
The benefits of Pulsar Security's red team engineers' certifications are multifaceted in a field where capabilities require more than just work experience to ensure an expert can address the latest technologies and security challenges. Such knowledge allows the team to test all your organization's security architecture and personnel. Not only that, our team has an in-depth understanding of modern cybersecurity concerns and strategies and proven years of professional, hands-on implementation experience. Simply put, our certifications in areas like Certified Ethical Hacking, OWASP Offensive Security, GIAC Certified Penetration Tester, GIAC Web Application Penetration Tester, and Offensive Security Certified Expert and Professional provide a benchmark for the red team's skills and capabilities.
The team's composition is designed to far exceed the remit of traditional security testing by meticulously challenging the effectiveness of technology, processes, policies, and personnel to detect and respond to highly targeted attacks that skilled cyber actors conduct over an extended period.

Duane Laflotte
As CTO, Duane works to resolve complex technical issues for the team and its partners. He can be found at the bleeding edge of emerging technology and believes that continually feeding curiosity results in prolonged growth and creative solutions to complicated challenges. Duane is an expert technologist in the areas of cryptography, exploit development, networking, programming, and enterprise data storage. As an industry leader, Duane has worked with a wide array of Fortune 500, government, and military organizations - such as Disney, Bank of America, the FBI, SOCOM, DARPA, and the NHL – as a solutions architect, red team lead, and presales engineer. Duane is a highly accomplished engineer who has achieved expert-level certification as an Offensive Security Certified Expert (OSCE) among other credentials such as Offensive Security Certified Professional (OSCP), GIAC Exploit Researcher & Advanced Penetration Tester (GXPN), Certified Ethical Hacker (CEH), Microsoft Certified Professional, and Microsoft Technology Associate. Duane is an active FIRST Robotics volunteer and has coached teams which have earned the prestigious Chairman's Award.




