What is WiGLE and Why is it Important to Your Network Security?
No, we’re not talking about gelatin snacks or dancing at home. WiGLE refers to the Wireless Geographic Logging Engine, and is accessible from https://wigle.net. It's essentially a global database that maps out the geographic location of hundreds of millions of wireless access points.
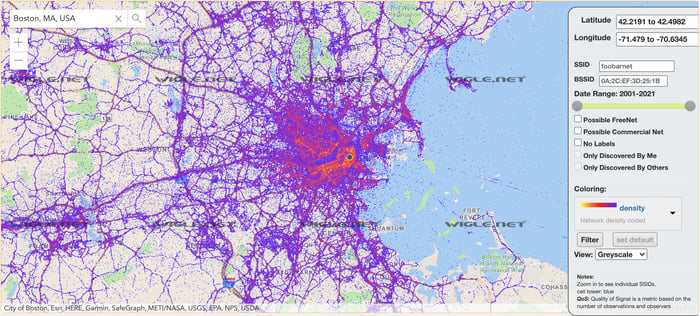
WiGLE search of Boston, MA
Before a hacker begins to attack a wireless network, they must first do research to make sure they’re targeting the right network. If the attacker lives in the same neighborhood as their victim their recon stage is a little easier. But what happens if the attacker lives on the other side of the country? How would this attacker learn about the wireless environment without being physically present?
This is where tools like WiGLE come into play.
How do hackers use WiGLE to attack remote Wi-Fi networks?
Recon First
If an attacker wanted to target a remote area, they would simply enter a zip code, address, or browse a map to learn what networks were present along with the network's approximate location. Then, by looking at a map of the target area, the attacker could search by network name (SSID) to decide what network to attack. If it's a busy metropolitan area, it's more difficult to pinpoint an exact location and differentiate one network from the other SSIDs, but it’s a good starting point.
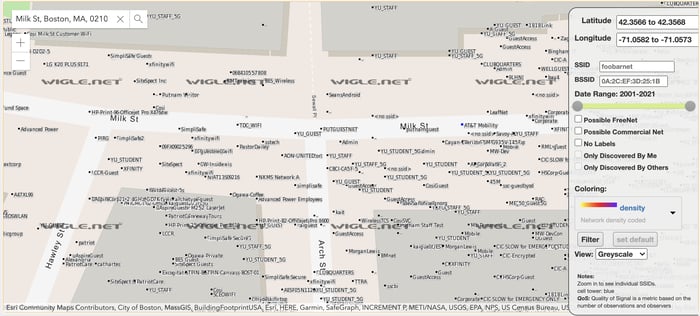 Closeup WiGLE Search of Milk Street, Boston MA
Closeup WiGLE Search of Milk Street, Boston MA
Another way an attacker leverages this data is to cross reference SSIDs with Preferred Network Lists (PNLs). In short, a PNL is a list of networks that a device has connected to previously, and has been approved by the device to willfully join again in the future if ever within broadcast range.
All access points (APs) that you have asked your device to "Connect Automatically" will be on your PNL...like a coffee shop or doctor's office. The PNL is how your phone knows that your home network is your home network and connects automatically when you get within range. That’s not to say that your phone will connect to any network with the same name - it would need the same password too - but your phone is constantly broadcasting out to the open airwaves “Are you my network?” to try to find home.
Recon leads to valuable information
If the attacker knows approximately where you live or work they can use WiGLE to note all of the SSIDs near your home or work. Armed with this information, they wait in another location (possibly a conference they know you're attending, or a coffee shop they know you frequent) and cross reference the lists of SSIDs gathered on WiGLE with activity from devices in locations they know you were in close enough proximity to gather the wireless traffic.
Take a minute to really think about how easy it is to capture network information.
Once the overlap between WiGLE data and gathered data with confirmed physical presence is determined, attackers can confirm which networks they need to target to attack your home or work network. And, the attack could be launched from anywhere close by, including a neighboring coffee shop, or even a weatherproof device dropped in the surrounding woods. The attack could also be launched from a distance of several hundred feet using specialized antennas. Attack scenarios are dependent on budget, availability, and motivation.
WiGLE also plays a good role
This isn’t to say that WiGLE can only be used for evil. One of its many other uses is to supplement legitimate site surveys to see what networks are in your area - an important consideration for your business, but it shouldn’t be used as your only survey.
Pulsar Security's automated, 24/7/365 Wi-Fi network assessment service, powered by SONAR, can assist you with the wireless landscape surrounding your business so you can protect your Wi-Fi networks from potential attackers

Ahren Thielker
Ahren is a versatile security expert, adept in both network and physical security. As a founding officer of the nonprofit organization TechRamp and an organizer of the BSides New Hampshire conference, Ahren is deeply committed to personal development and community empowerment. He excels in configuring firewalls, hacking web applications, and picking complex locks. Ahren has trained with the CORE Group as a physical security specialist and is a Core Netwars Tournament champion.




